Virtual private networks are becoming less and less effective over time as technological trends are changing. Relying only on a virtual private network for security might be quite risky. According to a business insider, cyberattacks still pose a threat to a company’s security after two years of work-from-home policies.
Businesses now must manage both on-premises and cloud-based workloads. Due to the widespread adoption of work-from-anywhere policies, they must adopt more effective solutions other than VPNs. Along with the security of a remote workforce, businesses require durable solutions that can be achieved by implementing VPN alternatives. Visit here for more information, https://nordlayer.com/blog/vpn-alternatives-for-business/.
VPN-based technologies face a significant problem as a result of these various needs. The need for alternatives that can securely authenticate users to secure your data, don’t impede connections, and grow with expanding hybrid IT infrastructures is growing as a result.
Why do Companies Need VPN Alternatives?

Source: unsplash.com
When expanding business networks into residences and other exterior settings, Virtual Private Networks have emerged as a better option. They provide a mechanism to transport data without making it accessible to other parties by enabling users to build secured connection gateways and adopt masked identities.
Even while many companies still use VPNs for all remote connections, all organizations must recognize a VPN’s limitations in providing cybersecurity. They should begin exploring alternatives, especially when handling the particular, specialized access requirements for various sorts of users. For many remote access use scenarios, particularly for third-party companies and suppliers, a VPN is not an appropriate all-purpose solution.
What are VPN’s Limitations?

Source: unsplash.com
VPNs contain several limitations that might put the organization’s security at risk:
Lack of Authentication
Due to the lack of thorough multi-factor authentication mechanisms in the majority of VPNs, these networks are more susceptible to identity theft and unlawful access.
Performance Issues
Network operations are made more difficult by VPNs’ reliance on external servers managed by a VPN service provider. Speed may suffer as a result of this added complexity and may cause problems with performance.
The remote workforce increases data processing and storage moving to the cloud. This process reduces the network and application performance. As a result, workers could try to establish a direct connection to cloud-based services. This will be depriving the company of network visibility and the opportunity to check traffic headed for the cloud for potentially dangerous information.
Limited Scalability
The performance of the network has been seriously harmed as a result of the unexpected increase in remote work. To mitigate the negative effects of subpar VPN performance on worker productivity, businesses and workers frequently implement unsafe solutions, such as the usage of divided VPNs or creating cached versions of critical data.
No Third-Party Protection
VPNs are not suitable for corporate networks that link to other businesses and suppliers. Network administrators typically are unable to observe network activities since they have little influence over how other parties utilize them.
What are the Best VPN Alternatives for Businesses Today?
The following are the best alternatives you can choose to replace the VPN technology in your organization:
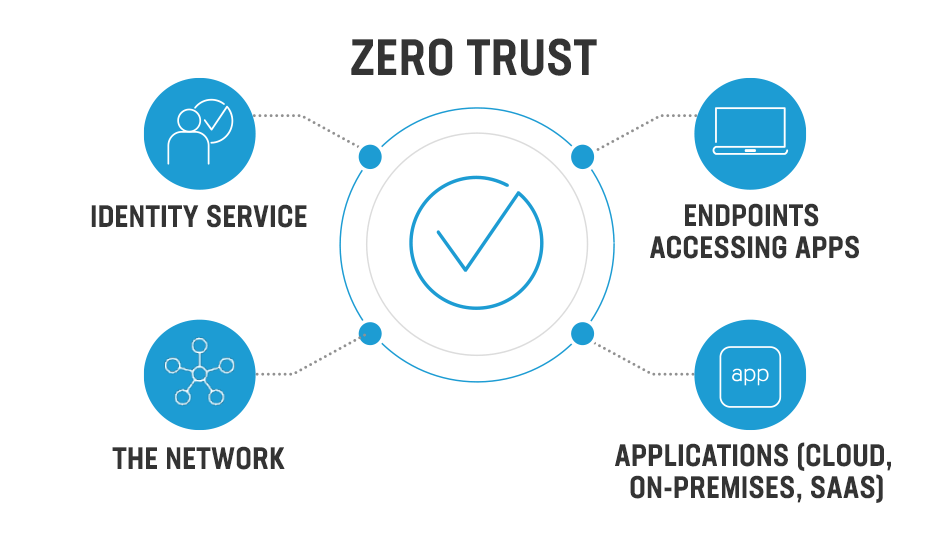
Zero Trust Security Model
Source: f5.com
An essential cybersecurity paradigm called “zero trust” is based on the idea that no user should have automatic access to a company’s network. By using this strategy, businesses may develop zero-trust systems in response to a user’s request for identification, authorization, authentication, and security posture.
Organizations may benefit from this security strategy’s ultimate zero-trust solutions, which include improved user experience, a simpler network environment, and increased defense against cyber threats. Another factor driving enterprises to embrace the zero-trust paradigm is the growing risk of unfiltered user access to their networks from a variety of devices.
Secure Access Service Edge (SASE)
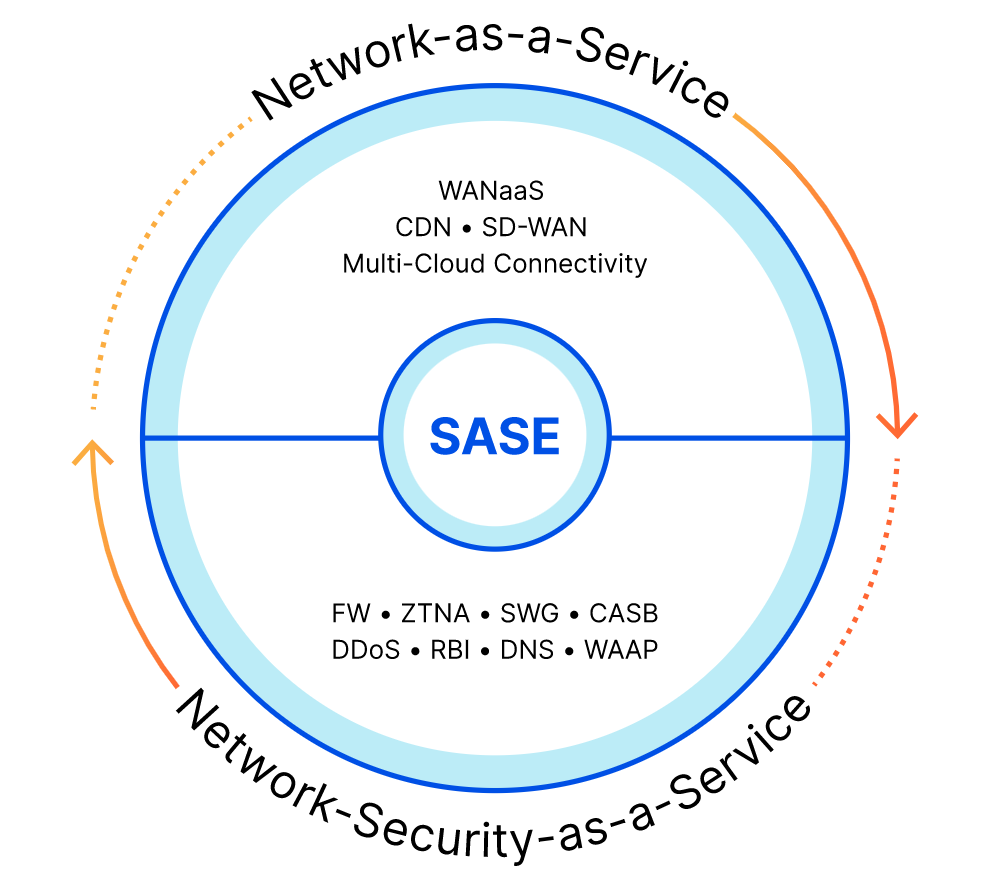
A contemporary cloud-based method for protecting the enterprise’s digital network from numerous dangers and fraud occurrences is the SASE security framework. SASE improves the connection and security features of the cloud. Wide-area connection is used to offer workers secure, all-inclusive service, wherever they may be.
The SASE platform consists of five key components that work together to secure the network beyond what is typically done. These components include:
- System-defined wide area network (SD-WAN),
- Secure web gateway (SWG),
- Firewall as a service (FWaaS),
- Zero trust network access (ZTNA),
- Cloud access security broker (CASB) (SD-WAN).
Using these components, SASE can provide secure access, reduce the likelihood of future cyber-attacks, distribute network traffic, and evaluate data flow. Moreover, SASE can authorize workers, limit their network access and mobility, and notify IT personnel when spyware is found.
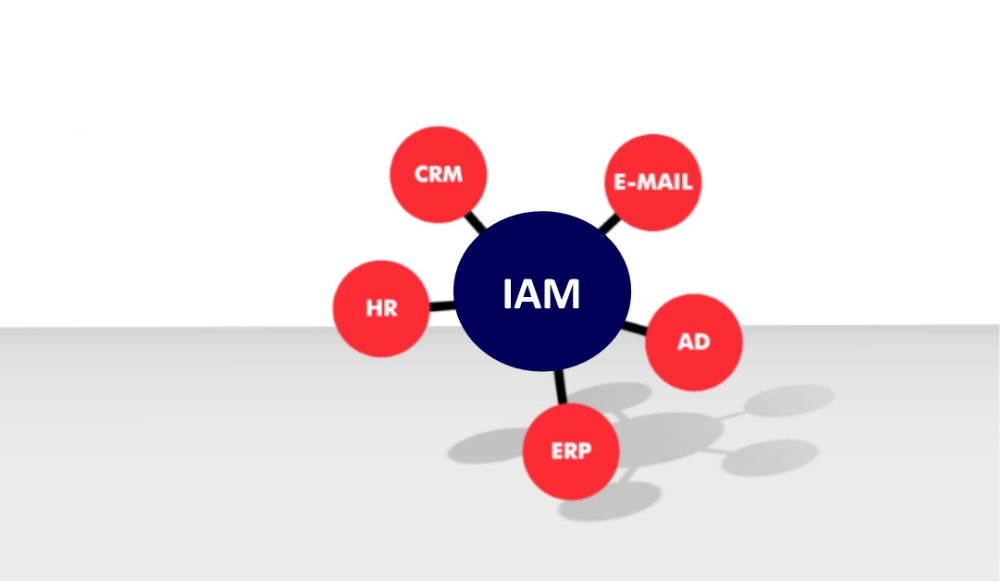
Identity Access Management (IAM)
Source: cybersecurity-excellence-awards.com
A VPN might benefit from additional security measures offered by an Identity and Access Management platform, or IAM. Identity management technology combines a thorough verification procedure to validate the legitimacy of all login attempts rather than only requiring a username and password. You may add multi-factor verification on top of the VPN connection using this approach. You may also provide them the authority by integrating it with your third-party dealer’s IAM solution.
Privileged Access Management (PAM)

Privileged access management technologies concentrate on maintaining sensitive information that has access to crucial tools and networks with a high standard of care and inspection. On the other hand, identity management creates the identity of specific users and authorizes them. PAM typically works in addition to IAM and offers a more complete solution.
PAM systems provide network administrators with the ability to specify user rights inside network boundaries. Managers may set the resources that are accessible to various access levels, enforce safe passwords, and keep an eye on accounts in real time.
Conclusion
Virtual Private Networks have no doubt proven their importance in cybersecurity but they have several loopholes that can put a company’s security at risk. Therefore, companies need to adopt several contemporary solutions as VPN alternatives that can help in securing full-fledged cybersecurity. The newly emerged cybersecurity solutions like SASE, IAM, and PAM are proving durable and efficient alternatives for businesses today.




